交換機配置mpls案例
- 0關注
- 0收藏,1938瀏覽
最佳答案

#
version 7.1.075, Release 7951P10
#
irf link-detect-time 100
#
clock timezone bj add 08:00:00
#
sysname Internet_XX_R1
#
forward-path-detection enable
#
ip vpn-instance vpn-1
route-distinguisher 65535:1
vpn-target 65535:1 import-extcommunity
vpn-target 65535:1 export-extcommunity
#
ip vpn-instance vpn-2
route-distinguisher 65535:2
vpn-target 65535:2 import-extcommunity
vpn-target 65535:2 export-extcommunity
#
router id 172.18.255.XX
#
ospf 1 router-id 172.18.255.XX
silent-interface Vlan-interface100
area 0.0.0.0
network 172.18.251.XX 0.0.0.7
network 172.18.255.XX 0.0.0.0
#
ospf 10 router-id 172.18.245.XX vpn-instance vpn-1
default-route-advertise summary cost 10
area 0.0.0.0
network 172.18.11.XX 0.0.0.7
#
mpls lsr-id 172.18.255.XX
#
mirroring-group 1 local
#
lldp global enable
#
system-working-mode standard
password-recovery enable
#
vlan 1
#
vlan 99
#
vlan 100
description SecManage
#
mpls ldp
#
interface NULL0
#
interface LoopBack1
ip address 172.18.255.XX 255.255.255.255
#
interface LoopBack10
description vpn-1 manage
ip binding vpn-instance vpn-1
ip address 172.18.245.XX 255.255.255.255
#
interface FortyGigE3/0/2
port link-mode route
shutdown
#
interface FortyGigE3/0/1
port link-mode bridge
port access vlan 100
mirroring-group 1 monitor-port
#
interface GigabitEthernet2/1/1
port link-mode route
#
interface GigabitEthernet2/1/2
port link-mode route
description to Internet_XXXX
ip binding vpn-instance vpn-1
ip address 172.18.11.XX 255.255.255.248
#
interface GigabitEthernet2/1/3
port link-mode route
#
interface GigabitEthernet2/1/4
port link-mode route
#
interface GigabitEthernet2/1/5
port link-mode route
#
interface GigabitEthernet2/1/6
port link-mode route
#
interface GigabitEthernet2/1/7
port link-mode route
#
interface GigabitEthernet2/1/8
port link-mode route
#
interface GigabitEthernet2/1/9
port link-mode route
#
interface GigabitEthernet2/1/10
port link-mode route
#
interface GigabitEthernet2/1/11
port link-mode route
#
interface GigabitEthernet2/1/12
port link-mode route
#
interface GigabitEthernet2/1/13
port link-mode route
#
interface GigabitEthernet2/1/14
port link-mode route
#
interface GigabitEthernet2/1/15
port link-mode route
#
interface GigabitEthernet2/1/16
port link-mode route
#
interface GigabitEthernet2/1/17
port link-mode route
#
interface GigabitEthernet2/2/1
port link-mode route
#
interface GigabitEthernet2/2/2
port link-mode route
#
interface GigabitEthernet2/2/3
port link-mode route
#
interface GigabitEthernet2/2/4
port link-mode route
#
interface GigabitEthernet2/2/5
port link-mode route
#
interface GigabitEthernet2/2/6
port link-mode route
#
interface GigabitEthernet2/2/7
port link-mode route
#
interface GigabitEthernet2/2/8
port link-mode route
#
interface GigabitEthernet2/2/9
port link-mode route
#
interface GigabitEthernet2/2/10
port link-mode route
#
interface GigabitEthernet2/1/18
port link-mode bridge
description to ACG
port access vlan 100
#
interface GigabitEthernet2/1/19
port link-mode bridge
description to IPS
port access vlan 100
#
interface GigabitEthernet2/1/20
port link-mode bridge
description to FW
port access vlan 100
#
interface M-GigabitEthernet0/0/0
#
interface Ten-GigabitEthernet2/4/1
port link-mode route
description to_Internet_Hexin_R1
ip address 172.18.251.XX 255.255.255.248
ospf network-type p2p
mpls enable
mpls ldp enable
mirroring-group 1 mirroring-port both
#
interface Ten-GigabitEthernet2/4/2
port link-mode route
#
interface Ten-GigabitEthernet2/4/3
port link-mode route
#
interface Ten-GigabitEthernet2/4/4
port link-mode route
#
bgp 65535
router-id 172.18.255.XX
timer keepalive 10 hold 30
group sddl internal
peer sddl connect-interface LoopBack1
peer 172.18.255.1 group sddl
#
address-family ipv4 unicast
peer sddl enable
#
address-family vpnv4
undo policy vpn-target
peer sddl enable
#
ip vpn-instance vpn-1
#
address-family ipv4 unicast
import-route direct
import-route ospf 10 med 10 route-policy dishi-sum
#
route-policy dishi-sum permit node 10
if-match ip address prefix-list dishi-sum
#
ip prefix-list dishi-sum index 10 permit XX
#
scheduler logfile size 16
#
line class aux
user-role network-operator
#
line class console
user-role network-admin
#
line class vty
user-role network-operator
#
line aux 0 1
authentication-mode scheme
user-role network-operator
#
line con 0 1
authentication-mode scheme
user-role network-admin
#
line vty 0 4
authentication-mode scheme
user-role network-admin
user-role network-operator
#
line vty 5 63
authentication-mode scheme
user-role network-operator
#
snmp-agent
snmp-agent local-engineid 800063A28030809BB9100000000001
snmp-agent community write private acl 2050
snmp-agent community read publc acl 2050
snmp-agent community read public
snmp-agent sys-info version v2c
snmp-agent target-host trap address udp-domain 172.18.250.253 params securityname private
snmp-agent trap enable arp
snmp-agent trap enable domain
snmp-agent trap enable mpls
snmp-agent trap enable radius
snmp-agent trap enable syslog
#
ssh server enable
ssh user sddl service-type all authentication-type password
ssh server acl 2000
#
ntp-service enable
ntp-service unicast-server 172.18.255.1
#
acl basic 2000
rule 10 permit source 172.18.250.0 0.0.0.255
rule 15 permit vpn-instance vpn-1 source 172.18.250.0 0.0.0.255
#
acl basic 2050
rule 0 permit source 172.18.250.253 0
#
undo password-control history enable
password-control aging 30
password-control length 8
password-control composition type-number 3 type-length 4
password-control login-attempt 3 exceed lock-time 30
password-control login idle-time 0
undo password-control change-password first-login enable
#
domain name system
#
domain default enable system
#
role name level-0
description Predefined level-0 role
#
role name level-1
description Predefined level-1 role
#
role name level-2
description Predefined level-2 role
#
role name level-3
description Predefined level-3 role
#
role name level-4
description Predefined level-4 role
#
role name level-5
description Predefined level-5 role
#
role name level-6
description Predefined level-6 role
#
role name level-7
description Predefined level-7 role
#
role name level-8
description Predefined level-8 role
#
role name level-9
description Predefined level-9 role
#
role name level-10
description Predefined level-10 role
#
role name level-11
description Predefined level-11 role
#
role name level-12
description Predefined level-12 role
#
role name level-13
description Predefined level-13 role
#
role name level-14
description Predefined level-14 role
#
user-group system
#
local-user root class manage
password hash $h$6$HrS5BEK+AYf1yVGN$i6S3EwbJquJuIgqvlJLVfUFPUqHjodMdROg15iLbAEuxo5p6jxzTwNNJoDerfBWHs+ZAtDNpZ8uM07LiNc38ZA==
service-type ssh terminal
authorization-attribute user-role network-admin
#
local-user xj class manage
password hash $h$6$LcQzdJThUIGoLYG7$oRxbZy0vOB4qVJAt5s2RKhrAExtleOju6fZMht7V6hrQlMG8YXC8l8xa0BALaLjFhJWG+CMfsoZycHaFFAp3qQ==
service-type ssh terminal
authorization-attribute user-role level-1
#
return
- 2023-09-19回答
- 評論(0)
- 舉報
-
(0)

您好,請知:
以下是MPLS VPN的配置案例,請參考:

組網說明:
本案例采用H3C HCL模擬器的S5820交換機來模擬MPLS VPN OPTION-B 典型組網配置。為了實現業務的相互隔離,需要將不同的VLAN綁定到不同的VPN實例中進行業務的互通,因此在本案例引入多實例VPN,將相關的業務進行捆綁。其中SW1屬於AS100,SW2屬於AS200,SW1與SW2的互聯使用trunk,允許VLAN 400 VLAN 500通過,最終建立EBGP鄰居關係,宣告業務網段,使得相同VPN實例的業務能互通,不同VPN實例的業務不能互通。
VPN實例規劃如下:
VPN實例名稱 | RD值 | RT值 | 業務類型 | 備注 |
vpn-rt | 100:1 | 100:1 | 實時業務 | |
vpn-nrt | 200:1 | 200:1 | 非實時業務 | |
IP地址規劃如下:
設備名稱 | 接口/VLAN | IP地址 | 子網掩碼位數 | 所屬VPN實例 | 備注 |
SW1 | Gi 1/0/2 | 10.0.0.1 | 30 | - | |
VLAN 10 | 192.168.10.1 | 24 | vpn-rt | ||
VLAN 20 | 192.168.20.1 | 24 | vpn-nrt | ||
Loopback 0 | 1.1.1.1 | 32 | vpn-rt | Router-id | |
SW2 | GI 1/0/2 | 10.0.0.2 | 30 | - | |
VLAN 100 | 172.16.10.1 | 24 | vpn-rt | ||
VLAN 200 | 172.16.20.1 | 24 | vpn-nrt | ||
Loopback 0 | 3.3.3.3 | 32 | Router-id |
配置步驟
SW1:
System View: return to User View with Ctrl+Z.
[H3C]sysname SW1
[SW1]int loopback 0
[SW1-LoopBack0]ip address 1.1.1.1 32
[SW1-LoopBack0]quit
[SW1]ip vpn-instance vpn-rt
[SW1-vpn-instance-vpn-rt]route-distinguisher 100:1
[SW1-vpn-instance-vpn-rt]vpn-target 100:1
[SW1-vpn-instance-vpn-rt]quit
[SW1]ip vpn-instance vpn-nrt
[SW1-vpn-instance-vpn-nrt]route-distinguisher 200:1
[SW1-vpn-instance-vpn-nrt]vpn-target 200:1
[SW1-vpn-instance-vpn-nrt]quit
[SW1]mpls lsr-id 1.1.1.1
[SW1]mpls ldp
[SW1-ldp]quit
[SW1]vlan 10
[SW1-vlan10]quit
[SW1]vlan 20
[SW1-vlan20]quit
[SW1]int vlan 10
[SW1-Vlan-interface10]ip binding vpn-instance vpn-rt
Some configurations on the interface are removed.
[SW1-Vlan-interface10]ip address 192.168.10.1 24
[SW1-Vlan-interface10]quit
[SW1]int vlan 20
[SW1-Vlan-interface20]ip binding vpn-instance vpn-nrt
Some configurations on the interface are removed.
[SW1-Vlan-interface20]ip address 192.168.20.1 24
[SW1-Vlan-interface20]quit
[SW1]int gi 1/0/3
[SW1-GigabitEthernet1/0/3]port link-mode bridge
[SW1-GigabitEthernet1/0/3]port link-type access
[SW1-GigabitEthernet1/0/3]port access vlan 10
[SW1-GigabitEthernet1/0/3]quit
[SW1]int gi 1/0/4
[SW1-GigabitEthernet1/0/4]port link-mode bridge
[SW1-GigabitEthernet1/0/4]port link-type access
[SW1-GigabitEthernet1/0/4]port access vlan 20
[SW1-GigabitEthernet1/0/4]quit
[SW1]int gi 1/0/2
[SW1-GigabitEthernet1/0/2]port link-mode route
[SW1-GigabitEthernet1/0/2]des
[SW1-GigabitEthernet1/0/2]ip address 10.0.0.1 30
[SW1-GigabitEthernet1/0/2]mpls enable
[SW1-GigabitEthernet1/0/2]mpls ldp enable
[SW1-GigabitEthernet1/0/2]quit
[SW1]bgp 100
[SW1-bgp-default]router-id 1.1.1.1
[SW1-bgp-default]peer 10.0.0.2 as-number 200
[SW1-bgp-default]address-family ipv4 unicast
[SW1-bgp-default-ipv4]peer 10.0.0.2 enable
[SW1-bgp-default-ipv4]import-route direct
[SW1-bgp-default-ipv4]quit
[SW1-bgp-default]address-family vpnv4
[SW1-bgp-default-vpnv4]peer 10.0.0.2 enable
[SW1-bgp-default-vpnv4]quit
[SW1-bgp-default]ip vpn-instance vpn-rt
[SW1-bgp-default-vpn-rt]address-family ipv4 unicast
[SW1-bgp-default-ipv4-vpn-rt]network 192.168.10.0 255.255.255.0
[SW1-bgp-default-ipv4-vpn-rt]quit
[SW1-bgp-default-vpn-rt]quit
[SW1-bgp-default]ip vpn-instance vpn-nrt
[SW1-bgp-default-vpn-nrt]address-family ipv4 unicast
[SW1-bgp-default-ipv4-vpn-nrt]network 192.168.20.0 255.255.255.0
[SW1-bgp-default-ipv4-vpn-nrt]quit
[SW1-bgp-default-vpn-nrt]quit
[SW1-bgp-default]quit
SW2:
System View: return to User View with Ctrl+Z.
[H3C]sysname SW2
[SW2]int loopback 0
[SW2-LoopBack0]ip address 3.3.3.3 32
[SW2-LoopBack0]quit
[SW2]ip vpn-instance vpn-rt
[SW2-vpn-instance-vpn-rt]route-distinguisher 100:1
[SW2-vpn-instance-vpn-rt]vpn-target 100:1
[SW2-vpn-instance-vpn-rt]quit
[SW2]ip vpn-instance vpn-nrt
[SW2-vpn-instance-vpn-nrt]route-distinguisher 200:1
[SW2-vpn-instance-vpn-nrt]vpn-target 200:1
[SW2-vpn-instance-vpn-nrt]quit
[SW2]router id 3.3.3.3
[SW2]mpls lsr-id 3.3.3.3
[SW2]mpls ldp
[SW2-ldp]quit
[SW2]vlan 100
[SW2-vlan100]quit
[SW2]vlan 200
[SW2-vlan200]quit
[SW2]int vlan 100
[SW2-Vlan-interface100]ip binding vpn-instance vpn-rt
Some configurations on the interface are removed.
[SW2-Vlan-interface100]ip address 172.16.10.1 24
[SW2-Vlan-interface100]quit
[SW2]int vlan 200
[SW2-Vlan-interface200]ip binding vpn-instance vpn-nrt
Some configurations on the interface are removed.
[SW2-Vlan-interface200]ip address 172.16.20.1 24
[SW2-Vlan-interface200]quit
[SW2]int gi 1/0/3
[SW2-GigabitEthernet1/0/3]port link-mode bridge
[SW2-GigabitEthernet1/0/3]port link-type access
[SW2-GigabitEthernet1/0/3]port access vlan 100
[SW2-GigabitEthernet1/0/3]quit
[SW2]int gi 1/0/4
[SW2-GigabitEthernet1/0/4]port link-mode bridge
[SW2-GigabitEthernet1/0/4]port link-type access
[SW2-GigabitEthernet1/0/4]port access vlan 200
[SW2-GigabitEthernet1/0/4]quit
[SW2]int gi 1/0/2
[SW2-GigabitEthernet1/0/2]port link-mode route
[SW2-GigabitEthernet1/0/2]des
[SW2-GigabitEthernet1/0/2]ip address 10.0.0.2 30
[SW2-GigabitEthernet1/0/2]mpls enable
[SW2-GigabitEthernet1/0/2]mpls ldp enable
[SW2-GigabitEthernet1/0/2]quit
[SW2]bgp 200
[SW2-bgp-default]router-id 2.2.2.2
[SW2-bgp-default]peer 10.0.0.1 as-number 100
[SW2-bgp-default]address-family ipv4 unicast
[SW2-bgp-default-ipv4]peer 10.0.0.1 enable
[SW2-bgp-default-ipv4]import-route direct
[SW2-bgp-default-ipv4]quit
[SW2-bgp-default]address-family vpnv4
[SW2-bgp-default-vpnv4]peer 10.0.0.1 enable
[SW2-bgp-default-vpnv4]quit
[SW2-bgp-default]ip vpn-instance vpn-rt
[SW2-bgp-default-vpn-rt]address-family ipv4 unicast
[SW2-bgp-default-ipv4-vpn-rt]network 172.16.10.0 255.255.255.0
[SW2-bgp-default-ipv4-vpn-rt]quit
[SW2-bgp-default-vpn-rt]quit
[SW2-bgp-default]ip vpn-instance vpn-nrt
[SW2-bgp-default-vpn-nrt]address-family ipv4 unicast
[SW2-bgp-default-ipv4-vpn-nrt]network 172.16.20.0 255.255.255.0
[SW2-bgp-default-ipv4-vpn-nrt]quit
[SW2-bgp-default-vpn-nrt]quit
[SW2-bgp-default]quit
PC都填寫IP地址:
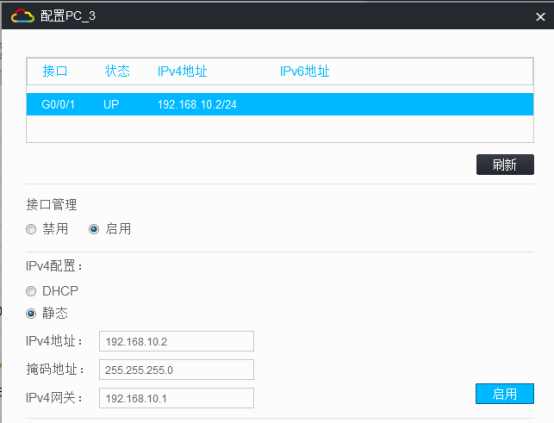
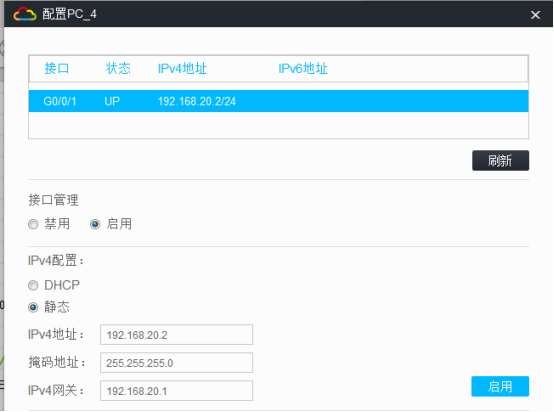
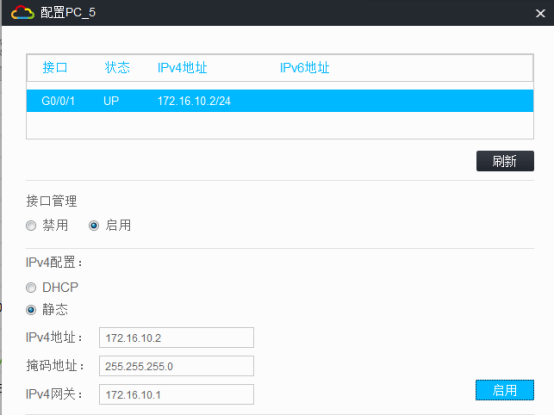
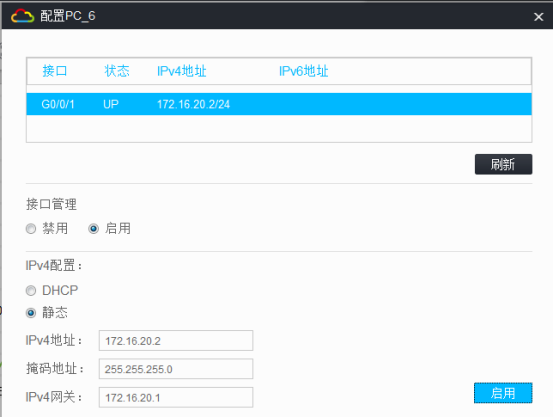
相同VPN實例的業務可以互通,不同VPN實例的業務不可以互通:
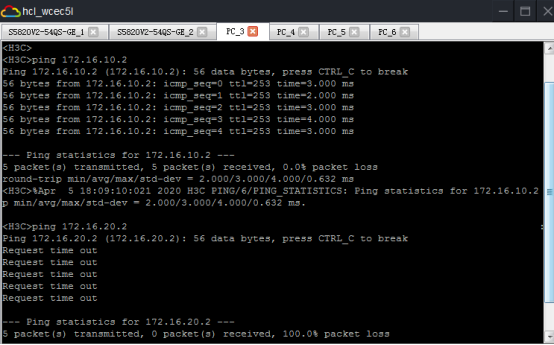
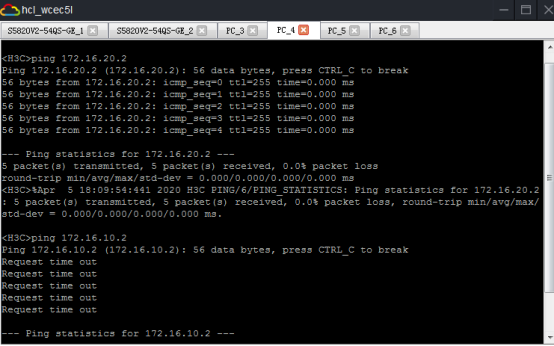
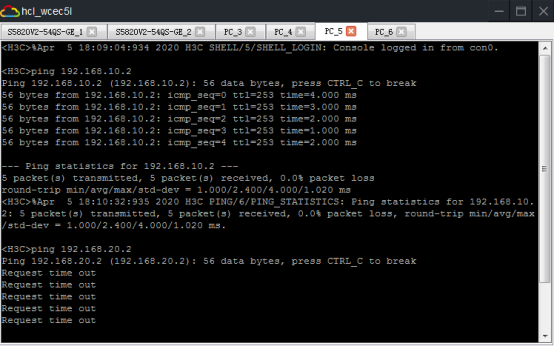
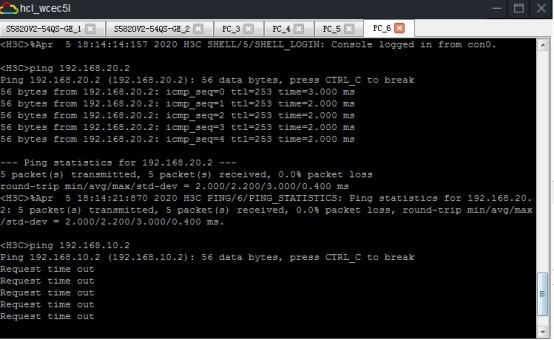
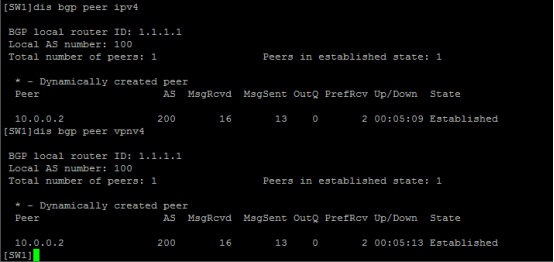
查看SW1的BGP鄰居信息:
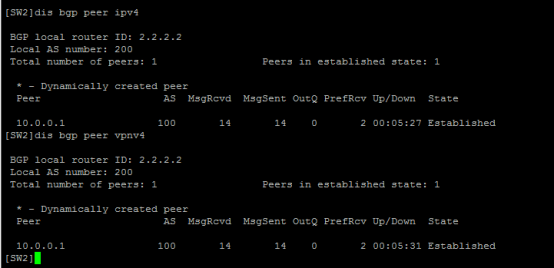
查看SW2的BGP鄰居信息:
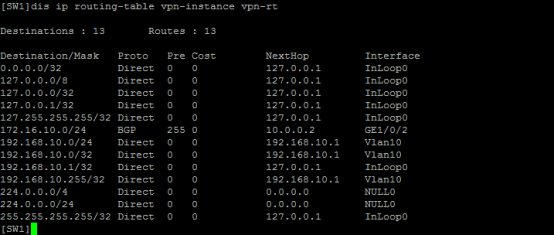
查看SW1的VPN路由表:
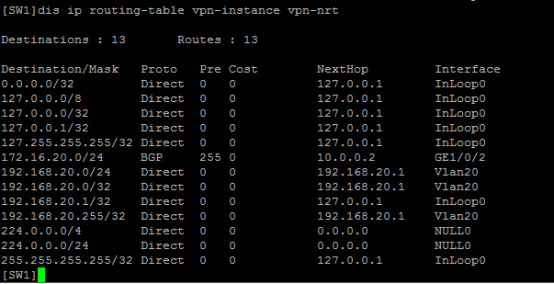
查看SW2的VPN路由表:
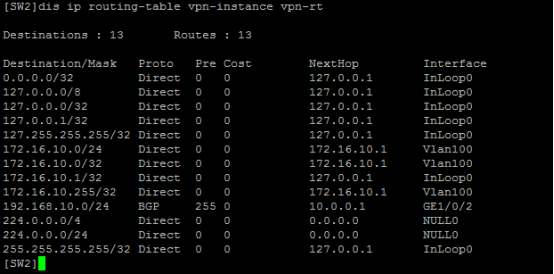

至此,S5820 MPLS VPN OPTION-B典型組網配置案例已完成!
- 2023-09-19回答
- 評論(0)
- 舉報
-
(0)
暫無評論
編輯答案


親~登錄後才可以操作哦!
確定你的郵箱還未認證,請認證郵箱或綁定手機後進行當前操作
舉報
×
侵犯我的權益
×
侵犯了我企業的權益
×
- 1. 您舉報的內容是什麼?(請在郵件中列出您舉報的內容和鏈接地址)
- 2. 您是誰?(身份證明材料,可以是身份證或護照等證件)
- 3. 是哪家企業?(營業執照,單位登記證明等證件)
- 4. 您與該企業的關係是?(您是企業法人或被授權人,需提供企業委托授權書)
抄襲了我的內容
×
原文鏈接或出處
誹謗我
×
- 1. 您舉報的內容以及侵犯了您什麼權益?(請在郵件中列出您舉報的內容、鏈接地址,並給出簡短的說明)
- 2. 您是誰?(身份證明材料,可以是身份證或護照等證件)
對根叔社區有害的內容
×
不規範轉載
×
舉報說明



暫無評論